The Wikipedia definition of the protocol starts like this: “Open Smart Grid Protocol (OSGP) is a family of specifications published by the European Telecommunications Standards Institute (ETSI). […] With over 4 million OSGP based smart meters and devices deployed worldwide it is one of the most widely used smart meter and smart grid device networking standards.”
While this reads like “copy-paste” art work taken straight from the “OSGP-DLMS/COSEM Interoperability” section of the OSGP web site, it definitly shows, that OSGP is not a “theory” but a standard that really is used “in the wild”.
RC4 and “Custom” Vulnerabilities
A research paper published in April 2015 with the title “Dumb Crypto in Smart Grids: Practical Cryptanalysis of the Open Smart Grid Protocol” has now outlined the core vulnerabilities of this widely used protocol. The authors Philipp Jovanovic (University of Passau, Germany) and Samuel Neves (University of Coimbra, Portugal) found:
- OSGP is using a “custom” algorithm for authenticated encryption (AE).
- The OSGP AE is based on the EN 14908 algorithm, the RC4 stream cipher and a “custom” OMA digest.
- All keys of the AE scheme are derived from the 96-bit Open Media Access Key (OMAK).
- “Given that the EN 14908 algorithm has a 48-bit key, it is already broken by design.”
- The custom OMA digest is “extremely weak, and cannot be assumed to provide any authenticity guarantee whatsoever.”
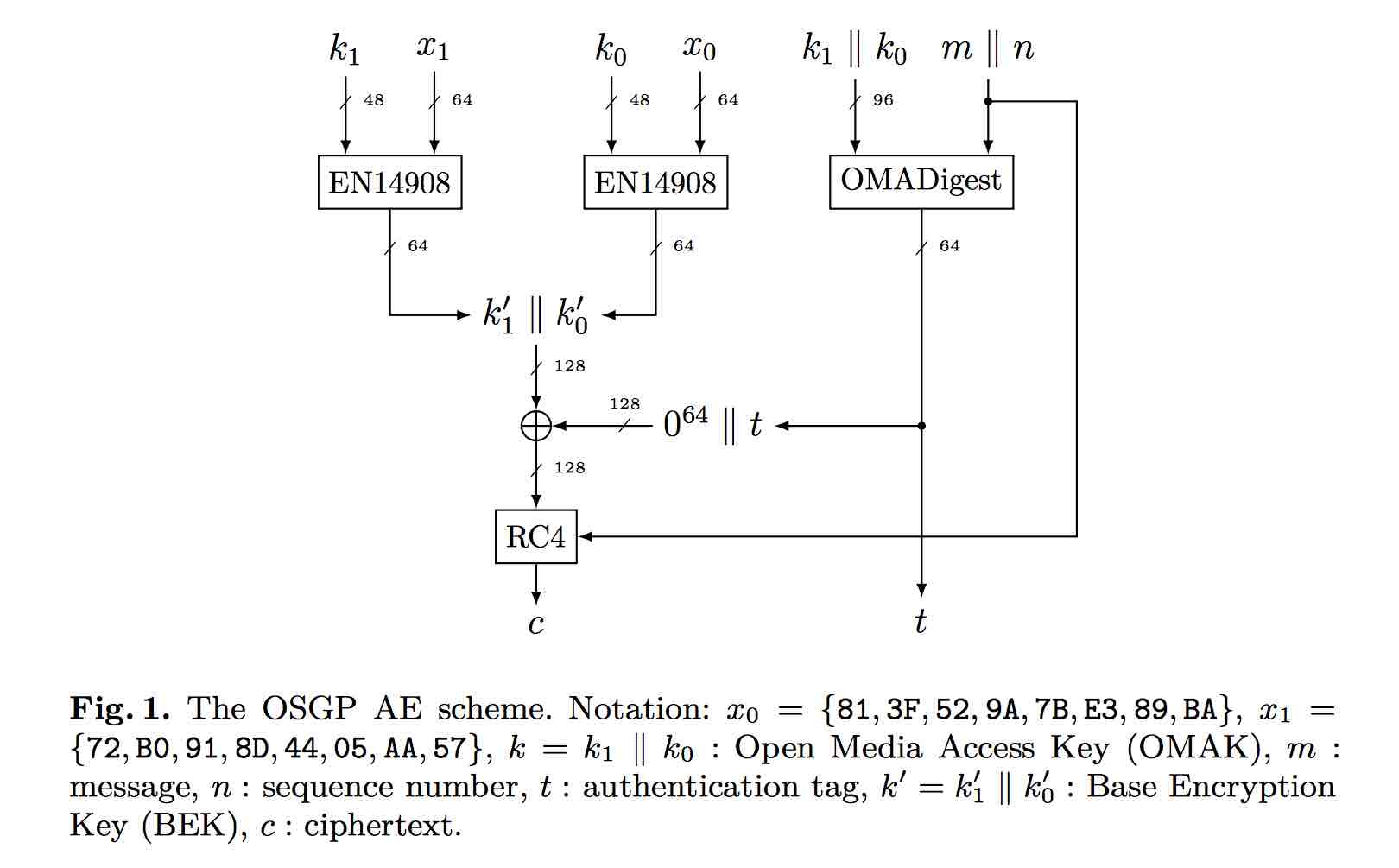
The above figure is from the research paper and shows the structure of the OSGP AE scheme.
… we describe further improvements [to existing attacks] which eventually allow us to mount fast forgery attacks on the OSGP AE scheme and furthermore enable recovery of the complete secret key and in this case all within the context of the protocol.
The paper shows why the OMAK “k” is at the center of the problem, and how it can be retrieved in “12 + 1 chosen-plaintext queries”.
But even for unknown OSGP ciphertext messages encrypted with the RC4 cypher it allows for attacks which can reach “key recovery in an average of 168 queries”.
Blame RC4?
The first RC4 vulnerabilites have been debated at least since back in 1995. However, most promissing attacks target the RC4 stream cypher and required analysing a large number of messages encrypted with one key.
In 2005 the “Klein’s attack” was presented which lead to tools that could break the RC4 based WEP WiFi encryption in around 1 minute with a probability of above 90%.
While OSGP uses RC4 in a “broken fashion” the even much weaker part is the OMA digest and the underlying OMAK key.
Blame LonTalk?
The authors also point out that the EN 14908 algorithm, which “is already broken by design”, originates from the industrial building and home automation network called LonTalk.
As of 2010 LonTalk was estimated to be implemented in over 90 million devices, which basically makes all related buildings vulnerable to trivial attacks … since decades and for decades to come.
Who cares?
Getting up to date?
Fixing all the crypto flaws in all the existing OSGP based devices might take a while even if the announced “next generation security specifications” will manage to come up with a viable solution. Existing devices might have hardware limitations which could prohibit the switch to a more robust algorithm.
The fact that the OSGP is not used in all (European) countries does not really matter when it come the the potential risk. Due to the nature of the interconnected European electric grid a disturbance which exceeds 3 GW in any part of the system (any country) has the potential to disrupt the entire grid.
All in all it is yet another proof that:
- so called “Smart Grid” technologies are and most likely always will be insecure.
- “custom” crypto systems are not a good idea.
- “broken by design” can be a legacy for many decades down the road.
References
- Philipp Jovanovic, Samuel Neves: “Dumb Crypto in Smart Grids: Practical Cryptanalysis of the Open Smart Grid Protocol”, [https://eprint.iacr.org/2015/428], 2015.04.27
- heise Online: “Verschlüsselte OSGP-Kommunikation von Smart Metern leicht belauschbar”, [http://www.heise.de/security/meldung/Verschluesselte-OSGP-Kommunikation-von-Smart-Metern-leicht-belauschbar-2642228.html], 2015.05.12
- Wikipedia: “RC4 stream cipher”, [https://en.wikipedia.org/wiki/RC4]
- Wikipedia: “Open smart grid protocol”, [https://en.wikipedia.org/wiki/Open_smart_grid_protocol]
- OSGP Alliance, “What is OSGP?”, [http://www.osgp.org/what-is-osgp/], 2015.05